Ensuring the cybersecurity of mobile machines
CRA, MVO, RED-DA - these are the terms used to describe the new EU directives that are creating new challenges for OEMs. Find out what tasks await you and how you can successfully meet them to not only protect your machines, but also secure a decisive competitive advantage. Ensure future-proof and compliant solutions!
Upcoming EU directives on cybersecurity
Over the next few years, the EU will introduce a series of new regulations that will significantly tighten cybersecurity requirements for manufacturers of machinery and equipment - especially OEMs.
The Radio Equipment Directive Delegated Act (RED-DA) focuses on the security of internet-connected devices with radio interfaces, including those that communicate via WLAN, cellular or Bluetooth.
In addition, the Machinery Ordinance (MVO) requires comprehensive security measures for machinery, control systems and safety-related software to protect against hacking and prevent tampering by providing complete evidence.
The Cyber Resilience Act (CRA) combines these and other regulations and requires OEMs to consider cybersecurity throughout the entire product lifecycle - from development to operation and decommissioning.
Mandatory security updates and vulnerability and incident reporting requirements will create a single framework across Europe, significantly raising the bar for manufacturers, importers and distributors. As a result, OEMs must adapt their processes, implement new standards and take early action to ensure not only compliance, but also a strategic competitive advantage.
RED-DA:
Radio Equipment Directive Delegated Act 2022/30
- Concerns manufacturers of products with radio interfaces
- Article 3.3 of the Radio Equipment Directive regulates the safety of radio equipment connected to the Internet
- Applies to devices that communicate e.g. via WLAN, cellular or Bluetooth, such as telemetry devices
- Also applies to products that can communicate with the Internet via a third party device
- Relevant standard: EN 18031 Cybersecurity for radio equipment
- EN 18031-1: Must not cause damage to networks
- EN 18031-2: Personal data must be protected
- EN 18031-3: Protection against fraud
EU-MR:
EU Machinery Regulation
- Applies transnationally in the EU
- Affects manufacturers, importers and dealers (including used machines)
- Includes hardware and software
- Safety-relevant software
- Safety-relevant components and machines with artificial intelligence
- Machines and control systems must be protected against hacker attacks
- Obligation to provide evidence of software attacks and modifications
CRA:
Cyber Resilience Act
- Combines EU-MR and RED-DA with regard to cyber security
- Supplements existing NIS 2 Directive (measures for a high common level of cybersecurity)
- Applies to all hardware and software with “digital elements/components”
- Affects manufacturers, importers and dealers
- Cyber security must be considered throughout the entire product life cycle - from planning and maintenance to decommissioning
- Security updates over the entire product life cycle (min. 5 years)
- Obligation to report vulnerabilities and incidents
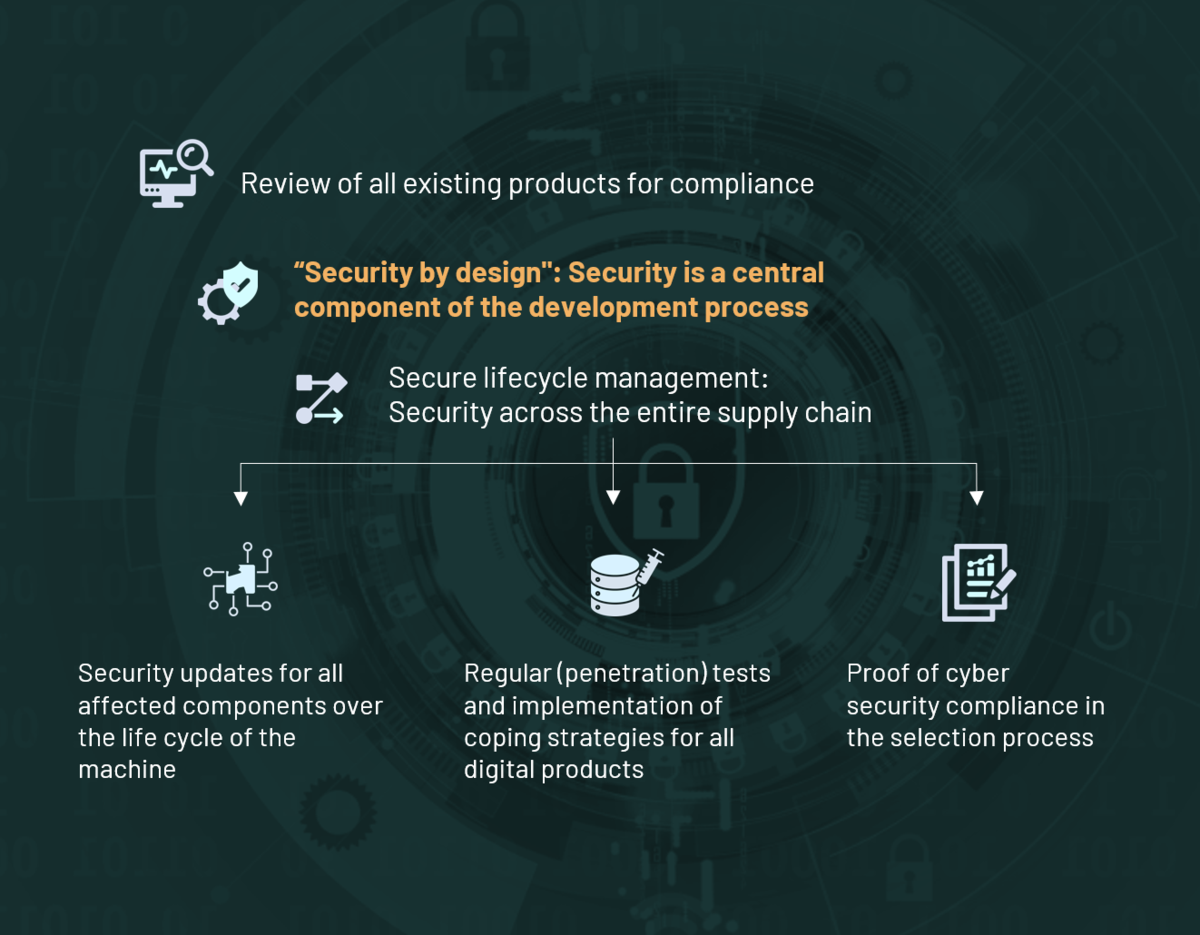
What must machine manufacturers ensure?
Manufacturers need to assess existing products for compliance and integrate security by design into the development process. Security measures are essential throughout the lifecycle of the device - from the supply chain to regular security updates. Digital products require continuous (penetration) testing to identify vulnerabilities and implement effective strategies to deal with damage. Proof of cyber security compliance is also mandatory in the selection process.
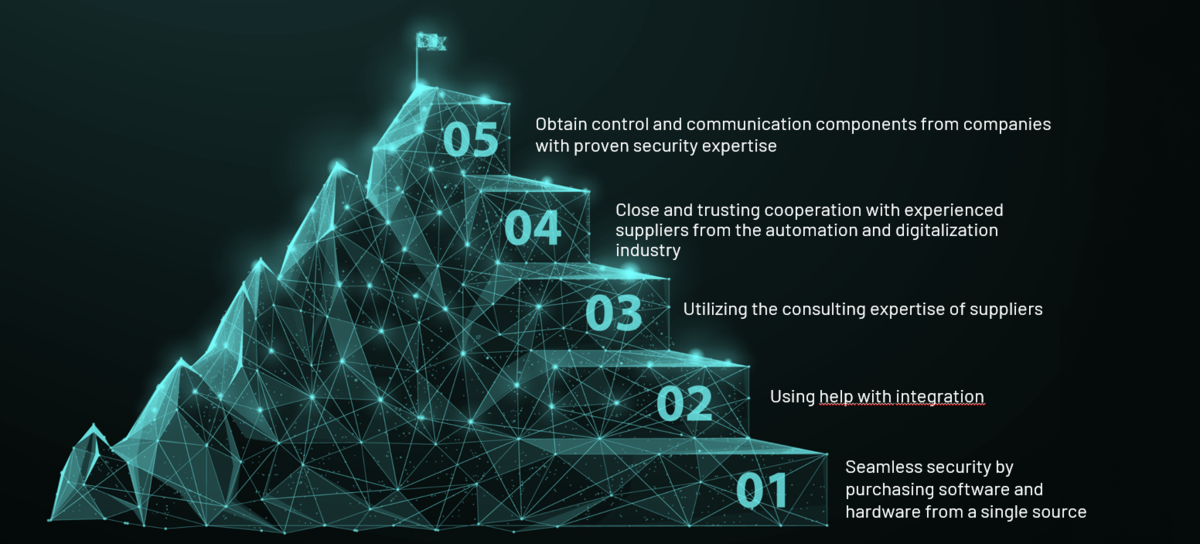
Resource and effort management
Compliance with the new regulations requires developing expertise in standards and guidelines, as well as hiring or training cybersecurity specialists. Alternatively, external consultants can be brought in. Independent auditors can help ensure compliance and mitigate risk. The requirements demand significant resources, but they are essential for future-proofing modern machines.
From the machine operator's perspective
Ongoing digitalization is increasingly affecting family-owned and small businesses. Millennials and Generation Z are taking over management positions and see the added value of digital processes. They are aware of security risks, demand transparency from manufacturers, and reject insecure systems. At the same time, competitive pressures are increasing, making efficient, secure and connected machines essential
Operators are also developing their own standards, such as QAA 4.0 in road construction, to digitalize processes such as the production, transport and processing of asphalt. This further increases the need for secure systems.
Many machines are left unprotected on construction sites, in forestry or in agriculture, making them particularly vulnerable to cyber attacks. Ransomware attacks on farmers or manufacturing companies can result in loss of data or control, threatening their very existence. Due to their size and mass, machines also pose a significant risk to third parties in the event of a loss of control. Operators and manufacturers alike risk their reputations.
Increasing digitalization and growing threats make it clear that more secure systems are not only a legal obligation, but also a critical success factor.
This is how STW helps with security compliance
At STW, we understand the challenges machine manufacturers face in meeting security and compliance requirements. Our solutions enable you to make your machines secure and future-proof.
Efficient security and update management:
Our cloud platforms provide the ideal foundation for professional security and update management. Security updates can be installed quickly and reliably via the cloud, whether for a single device or an entire fleet of machines.
Flexible scalability:
Our system is fully scalable and adapts to your needs. From small family-owned businesses to large fleet operators, we offer a centralized solution that works both individually and on a large scale.
Already well prepared today:
Our hardware and software already meet many of the requirements of the Cyber Resilience Act (CRA). This gives you the peace of mind of not only being compliant, but also having a technological advantage.
Practical tools for easy deployment:
We make it easier for you to implement cybersecurity and safety policies with specially designed software mechanisms and tools. These features are designed to simplify compliance while ensuring the highest standards of security.
Easy integration for OEMs:
Original Equipment Manufacturers (OEMs) who rely on our STW framework benefit from easy implementation of the required security mechanisms. Our system is designed to help you implement security policies easily and efficiently.
With STW, you have a partner that not only helps you meet regulatory requirements, but also helps you make your machines secure and competitive.
Complete, consistent and secure data is the foundation for many services related to mobile devices. STW addresses these needs with network modules, software tools and services, providing flexibility, visibility and scalability for digital transformation.
The TCG-4 data management module goes far beyond simple tracking or logging. In addition to precise positioning and CAN bus data acquisition, it enables data pre-processing and communication via WiFi and 4G to cloud solutions - standard or customized. This opens up new possibilities, including predictive maintenance.
Starting in 2026, the TCG family will be expanded: the TCG-5 integrates AI-based object recognition via camera connection, increases positioning accuracy via RTK, and works without GNSS thanks to an external IMU. 5G will also enable V2X communication. In parallel, the TCG.nano is being developed with a reduced feature set as a gateway and data logger.
All platforms are based on freely programmable Linux, complemented by STW tools for quick deployment and configuration. Users benefit from scalability across the entire machine park. The TCG modules meet the high quality standards of mobile machines.
The demands on electronic control systems for mobile machinery are increasing. There are functional safety regulations, the requirements of the EU's Cyber Resilience Act, but also the need for greater operator support as we move towards autonomous machines. As machines become more complex, so does the complexity of software. To help our customers, our 4th generation ESX family offers not only scalable solutions in terms of I/O configuration and performance, but also tools and services that address all of these challenges.
Our flagship ESX.4cl-ag is the standout product, featuring not only a 6-core Infineon Aurix processor (with a dedicated core for fail-safe applications), but also an optional co-processor with a Linux system, ideal for parallel processing of large amounts of data. The rugged design ensures long-term operation under extreme conditions without the need for active cooling.
The consistent use of the processor architecture across the entire family allows easy porting of the application and thus fast adaptation to the machine size or functionality. This is facilitated by our open source tool openSYDE and the various programming options in "C" or IEC61131-3 or model-based design in Matlab / Simulink.
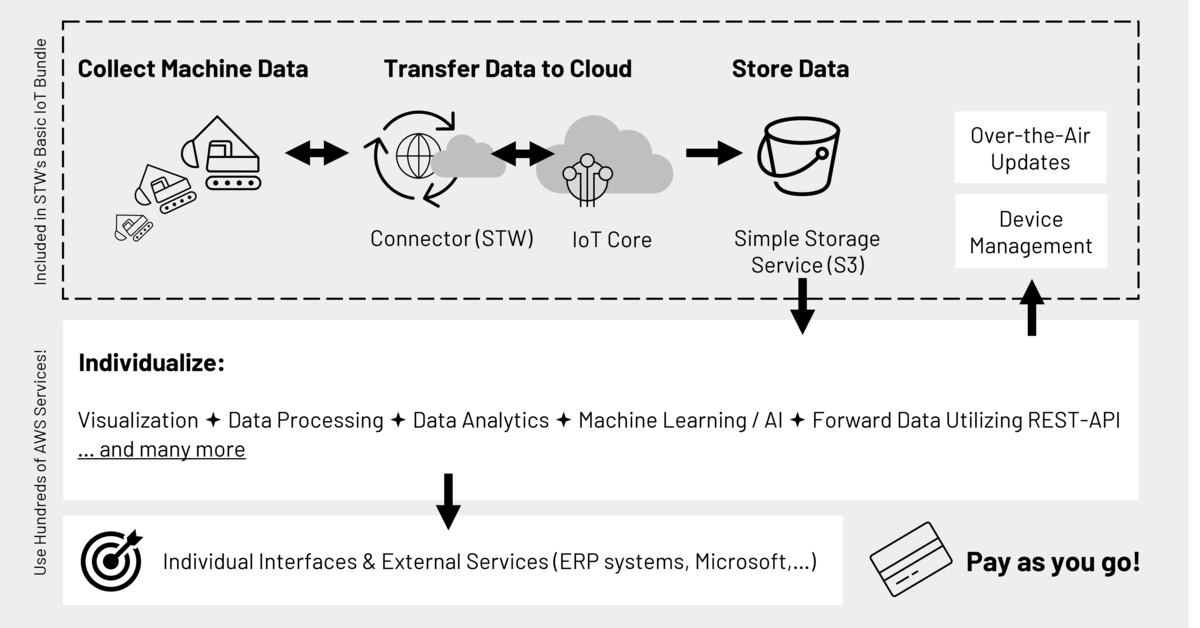
Our IoT services for your seamless, secure integration
With our Basic IoT Bundle, you can instantly connect your machine infrastructure and data to an industry-standard cloud service. You get the ability to use secure over-the-air updates and manage your devices and SSL certificate rotation. This way you comply with requirements on cyber security. Collect machine data, transfer it encrypted to your cloud account and store it in a bucket. On the machine side, you can easily use our TCG solutions, which come pre-configured with the appropriate cloud connector.
Once the data is available in the cloud, you can use hundreds of highly customizable services such as visualization, data processing and analysis, machine learning or AI and even forward data via a REST API (REST = Representational State Transfer, i.e. the transition from one state to the next represented by the transferred data). The adaptation of individual interfaces to external services such as ERP or CRM systems or Microsoft Azure is also easy to implement. Basic support, tips and tricks are available from our field application engineers. Implement your IoT business ideas yourself - independently or with the help of STW or an AWS partner.
These STW security measures already protect mobile machines today
Consulting and support
- Team of hardware and software specialists
- Product Security Incidence Response Team (PSIRT) closes emerging security gaps
- Vulnerability monitoring and risk analysis for existing hardware and software
- Regular penetration tests check security against hacker attacks
- Zero day detection: proactive security analyses of the software
- Security workshops for OEMs as part of the STW Academy
- Individual support to fulfil the security requirements of customer applications
Secure competitive advantages today
Machine manufacturers that are already RED-DA-/EU-MR-/CRA-compliant today,
- offer customers security for their data
- provide customers with transparency and thus enjoy greatertrust
- demonstrate a sense of responsibility and innovative strength
- have the opportunity to sell corresponding security concepts and services
- secure their long-term competitiveness today
- benefit from increased attractiveness of their offerings
1. Security Analysis
Your gateway to cybersecurity for mobile machines - clear, competent and future-proof.
Our security analysis is the foundation for a secure future. In a compact health check, you get in-depth knowledge from experienced experts. We analyze your applications, processes and development artifacts in a targeted manner - flexibly, either remotely or on-site.
Contents at a glance:
- Introduction to current and future security regulations
- Specific analysis of your individual customer application
- Clear overview of applicable norms and standards
- Recommendations for action and definition of next steps
Added value for you:
- Defined timeframe & transparent costs
- Workshop, online meeting, on-site, off-site
- Maximum flexibility through broad expertise
You get not only a security assessment, but also a roadmap for the next steps. Use this introduction to define your next steps - with the right services from our portfolio!
2. Security Risk Analysis (TARA) & Cybersecurity Concept Consulting
Our risk analysis and cybersecurity design consulting services can help you lay the groundwork for robust, future-proof products. We offer a structured approach that is customized to your hardware and software. We identify possible attack scenarios and assess the risk. Benefit from our experience and existing STW hardware and software data.
Services at a glance:
- Risk assessment - Identify and analyze potential security risks
- Asset identification - Identify components and systems worth protecting
- Threat analysis - derive possible attack scenarios
- Define countermeasures - plan specific security measures
- Result - "Countermeasure Requirements & Goals" as the basis for your security concept
Flexible & tailored to your needs: advice is tailored precisely to the specifics of your hardware and software.
Added value for you: A tailor-made security concept that minimizes your risks and lays the foundation for comprehensive cyber security.
3. Vulnerability Scan
Security for your STW hardware: Our Vulnerability Scan provides you with a reliable and accurate security check of your applications - the basis for CRA compliance and a secure future.
Services at a glance:
- Per Application/Scan
- Flexible and targeted per application
- Binary image or SBOM
- Get a clear statement of CRA compliance
- Is the SBOM missing? We create it for you from the provided binary image
- Automated vulnerability notification
- Daily, nightly scans with immediate notification of newly discovered vulnerabilities
Want to keep an eye on vulnerabilities associated with third-party hardware? Benefit from our expertise and state-of-the-art tools.
Added value for you: Early detection of vulnerabilities, continuous monitoring, and clear recommendations for action - efficiently, automatically, and compliantly.
4. Cyber Security Penetration Testing
Find hidden vulnerabilities before anyone else!
Secure systems need reliable testing. Using state-of-the-art methods and tools, we simulate realistic attacks on your systems to identify potential vulnerabilities and show you how to fix them.
Penetration testing services:
- Embedded Device Penetration Testing
- Thorough testing of your embedded systems
Added value for you: We use targeted attacks to uncover hidden vulnerabilities before they can be exploited by attackers. You receive clear recommendations for securing your systems that are effective, transparent, and practical.
Competent support
We're here to help you!
New EU directives such as the Cyber Resilience Act present complex challenges for many organizations. At STW, we won't leave you to deal with them alone. Our experts have in-depth knowledge of current regulations and can help you implement them efficiently and compliantly.
Whether you have technical questions, need help implementing security mechanisms, or want to review your processes for compliance, our team is here to assist you. With our extensive experience and practical solutions, we can guide you on your path to greater security and compliance.
Rely on our expert support to make your machines and systems fit for today and tomorrow. We're here for you!